CA Certificate
Last update:2024-03-06 17:04:53
Add CA Certificates
CDN node support secure communication with clients through mTLS mutual authentication. There are two main configuration operations:
- Enable client-to-server authentication (one-way authentication): Upload the server certificate (public key + private key) and associate a domain name;
- Enable server-to-client authentication (mutual authentication): Upload the client root certificate and enable client-to-server authentication configuration.
Configure both the client and CDN nodes to enable mTLS mutual authentication. Before enabling this feature, please upload the server certificate files and the client CA root certificate files first.
How to Upload a CA Certificate
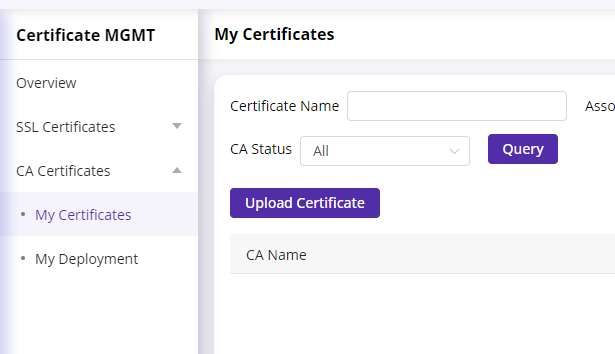
Log in to CDNetworks Console , click [Certificate MGMT] - [CA Certificate] - [My Certificate].
Click “Upload Certificate” button. You can choose to import a certificate or copy the certificate content to add a new certificate.
Uploading a Certificate
Select the CA type: Root CA or Sub-CA. If it’s a Sub-CA certificate, please select the associated Root CA.
CA Name: The name of the CA certificate.
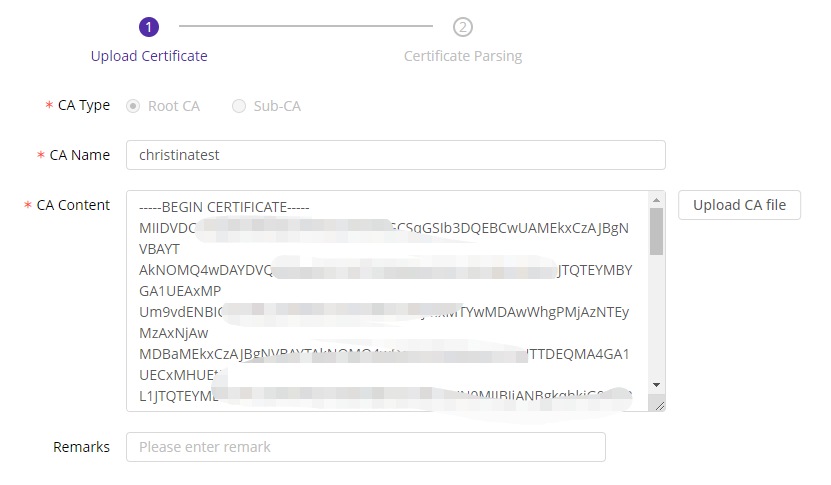
CA Content: You can upload a CA file for CA content analysis.
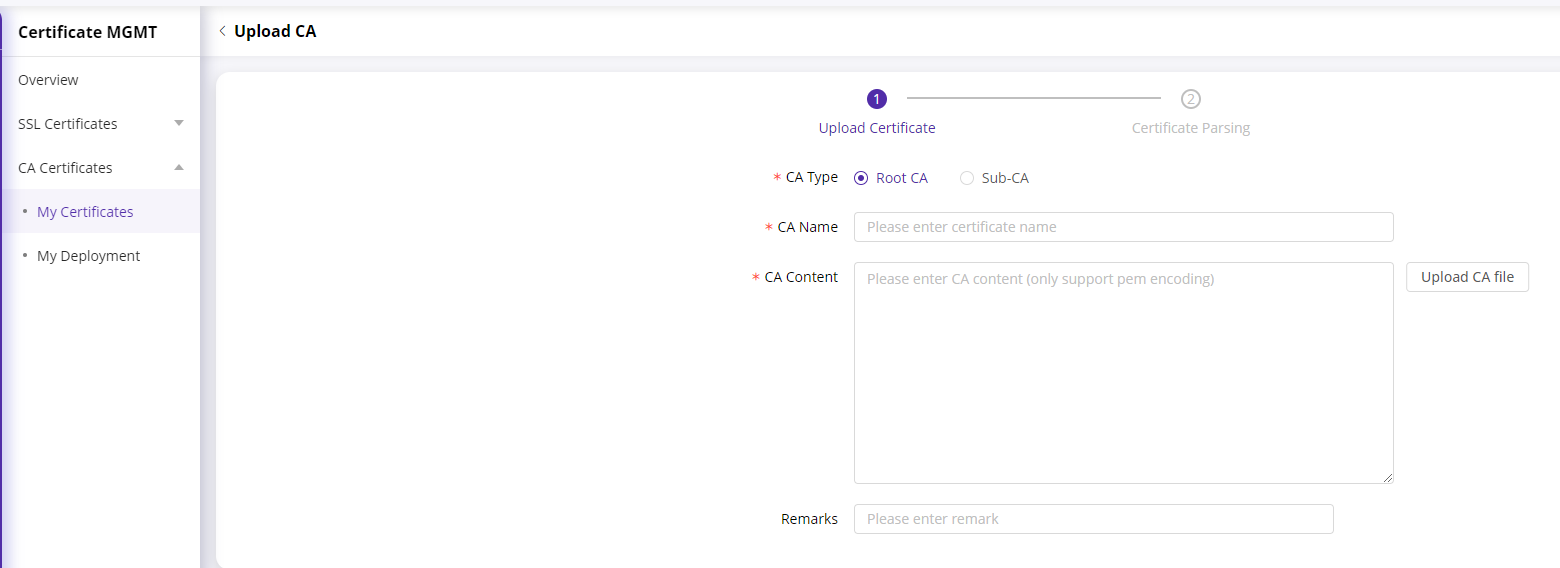
Click next to proceed with the certificate analysis.
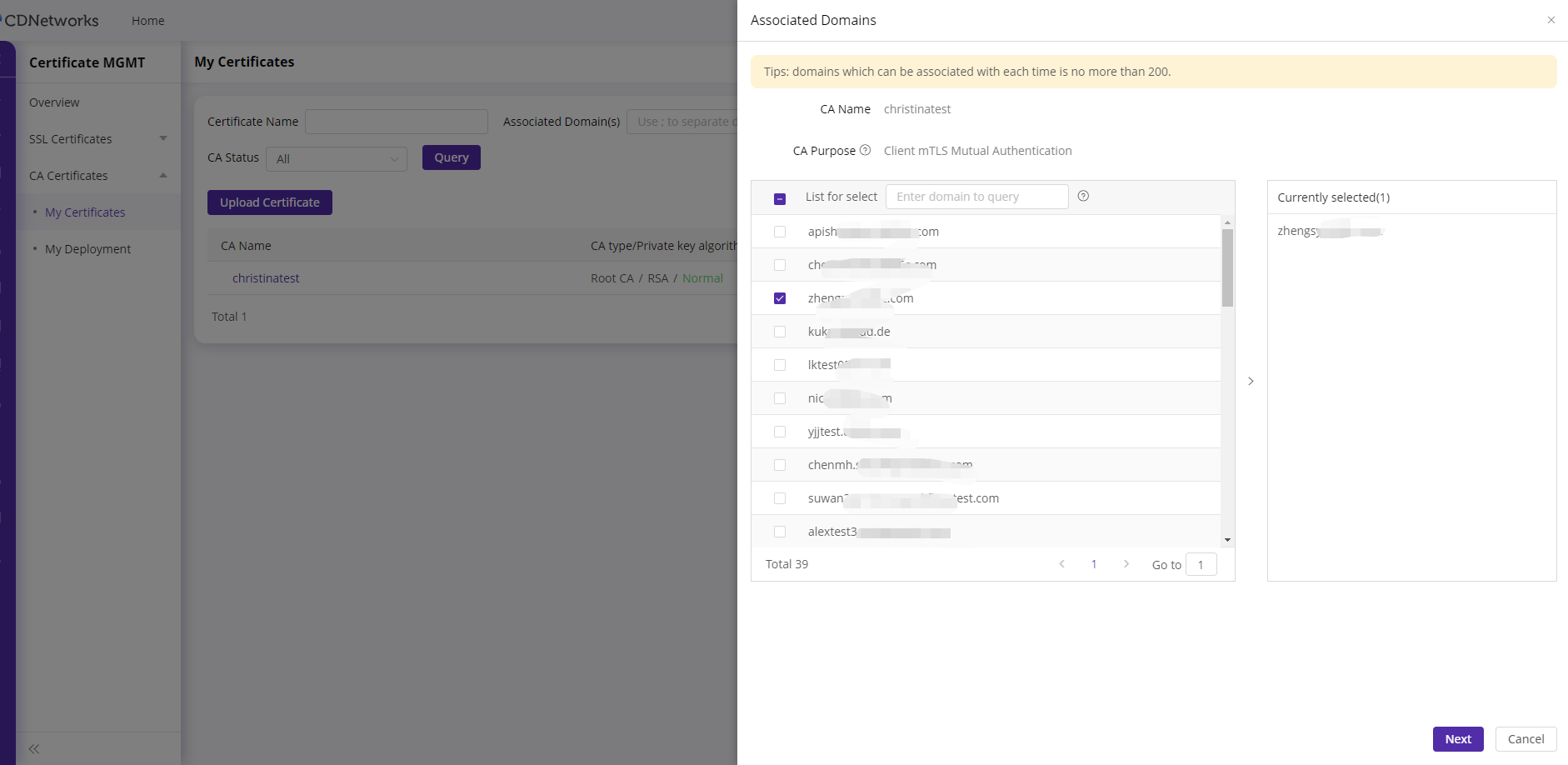
Associating a Domain Name with a CA Certificate
Select a CA certificate and click “Associate Domain.” Then, check the domains you wish to associate for the certificate deployment.
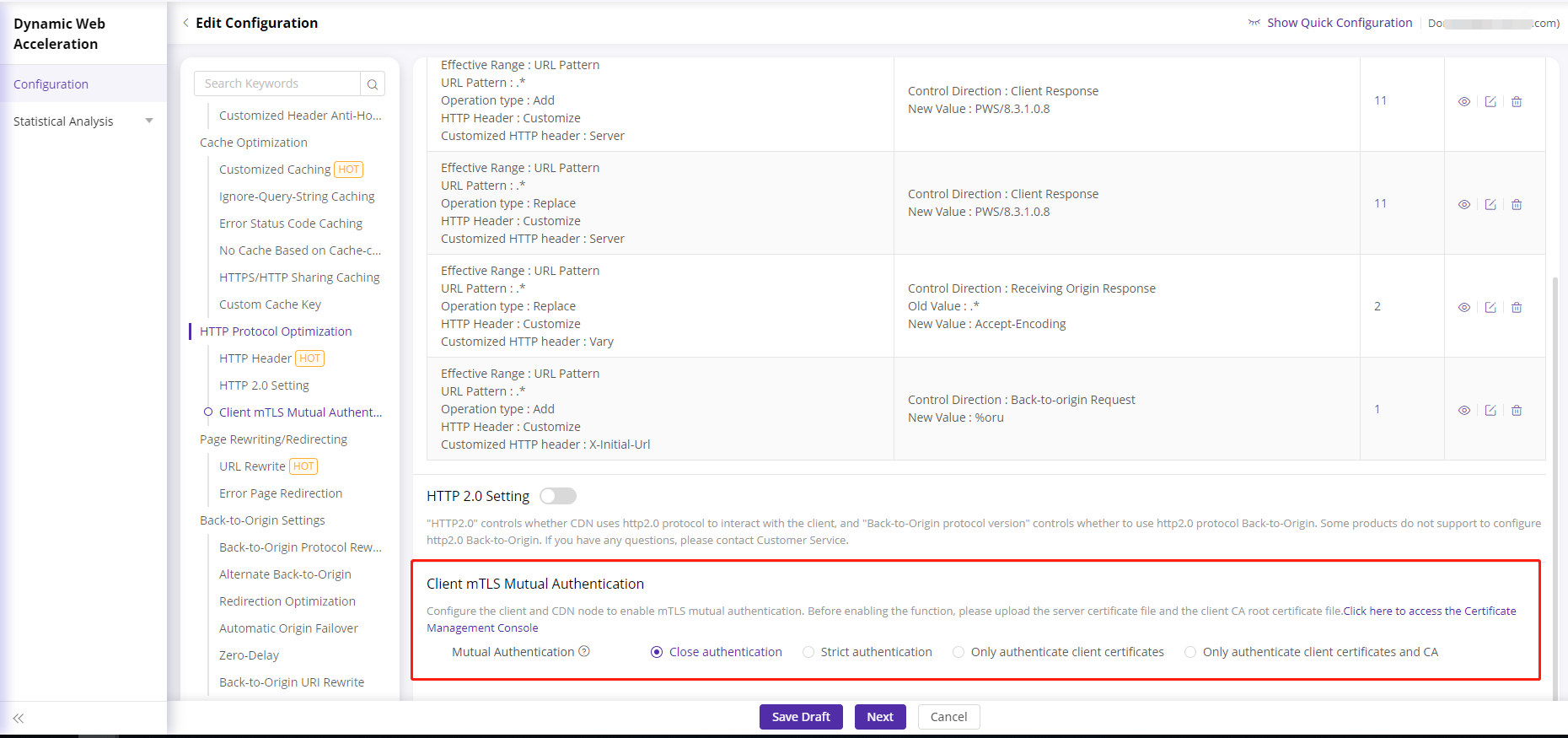
Client mTLS mutual Authentication Configuration
There are four modes as follows:
- Strict Authentication: It means that the node strictly verifies the validity of the client certificate and the credit status of the certificate authority, and the request cannot be connected normally if the verification fails. Before selecting this configuration, the associated CA certificate must be configured first.
- Only authenticate client certificates and CA: Indicates that the node only verifies the validity of the client certificate and the trust of the certificate authority, and the request that fails the verification can still be connected normally. It is recommended to configure the associated CA certificate before selecting this configuration.
- Only authenticate client certificates: Indicates that the node only verifies the client certificate, and does not verify the credit status of the certificate authority, and the request that fails the verification can still be connected normally. It is recommended to configure the associated CA certificate before selecting this configuration.
- Close authentication: Indicates that the node does not verify client certificates. Selecting this configuration does not need to configure the associated CA certificate.
Edit CA Certificates
Editing the certificate involves updating the certificate content. When the certificate is updated, it must be timely updated on CDNetworks to prevent the old certificate from becoming invalid.
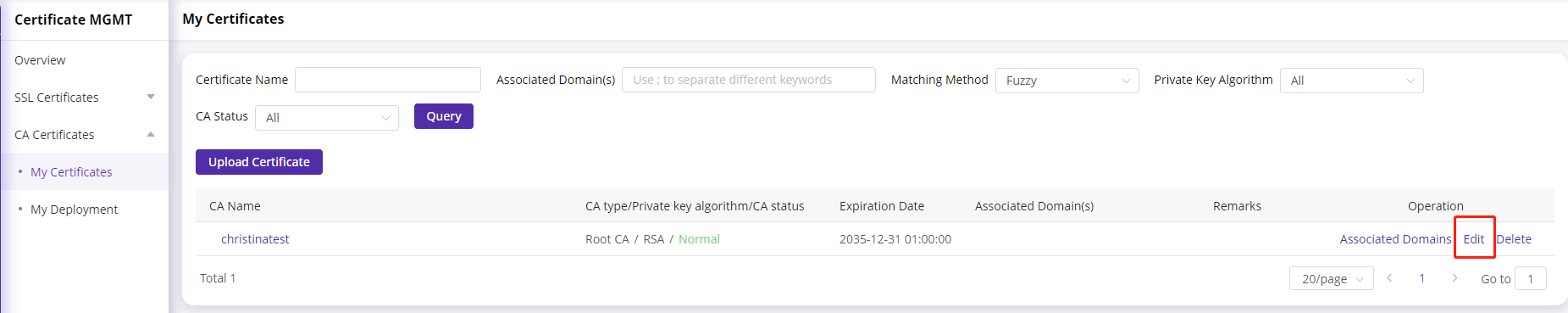
- Log in to CDNetworks Console , navigate to [Certificate MGMT] - [CA Certificate] - [My Certificate].
- Click the [Edit] button in the right-hand operation area.
- Enter the editing page and edit the CA name, CA content, and remarks.
Delete CA Certificates
A certificate can only be deleted if it has no sub-certificates and is not associated with any domain name.
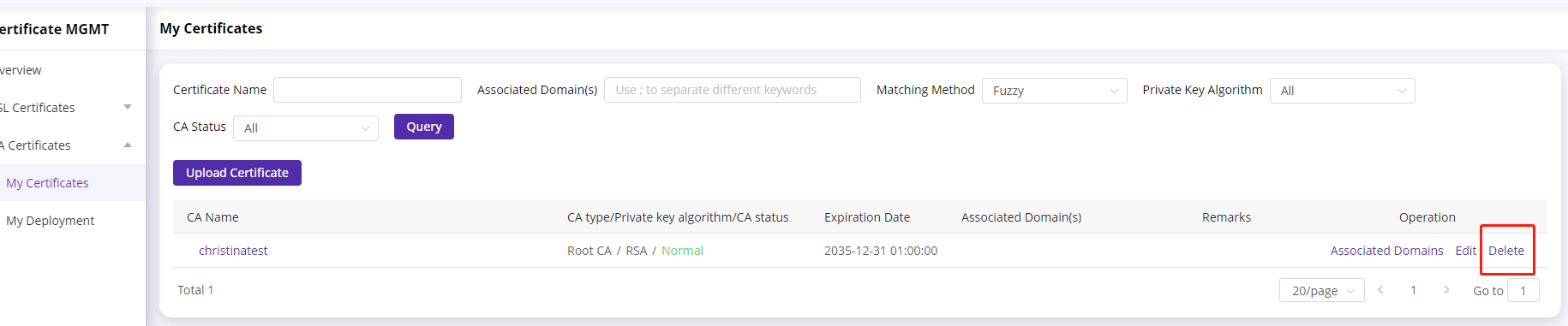
- Log in to CDNetworks Console , navigate to [Certificate MGMT] - [CA Certificate] - [My Certificate].
- Click the [Delete] button in the operation area on the right side of the list.
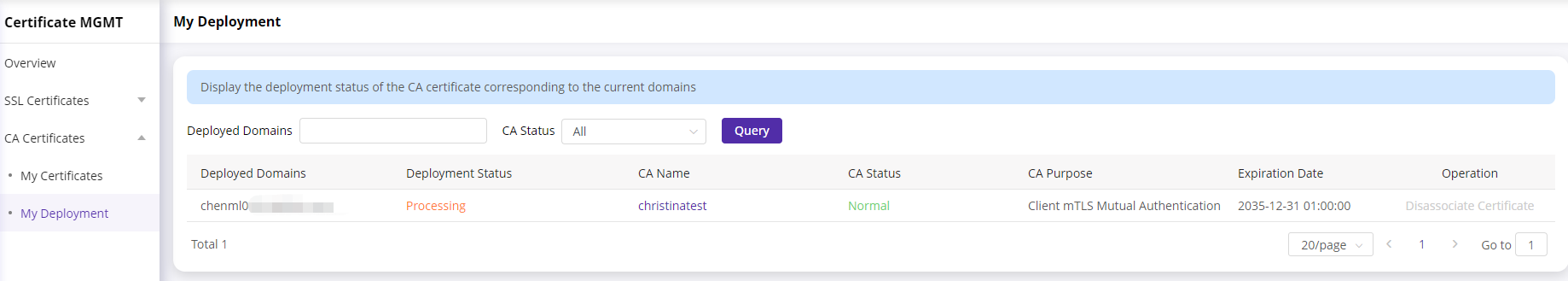
My Deployment
This page provides information on deployed domain lists with your private TLS certificates. you can deassociate your own TLS certificates from your acceleration domains by clicking ‘Deassociate Certificate’
Even if your TLS certificates are expired. you should deassociate the TLS certificates from your acceleration domains.
You sign up to CDNetworks Console , click [Certificate MGMT] - [CA Certificate] - [My Deployment]