Dashboard
Last update:2025-02-21 11:40:04
The Dashboard page displays the number of protected hostnames, product updates, and a summary and trend of requests. Through this page, you can:
- Know the number of accessed hostnames and whether their protection is enabled.
- Understand the overall protection status by viewing the requests trends of the websites.
Go to Dashboard:
- Log in to the CDNetworks Console, find the security product in use under Subscribed Products, and click to enter.
- Go to Dashboard.
View the protected hostnames
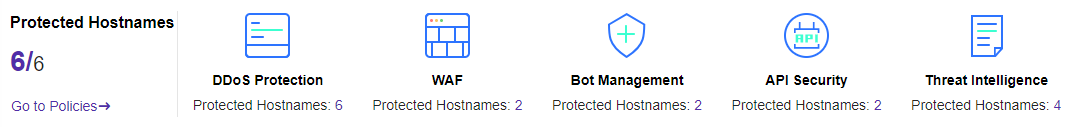
- Number of protected hostnames: The total number of hostnames that they have at least one security policy enabled.
- Total number of hostnames: The Total number of accessed hostnames.
- Number of hostnames with security policy: The number of hostnames that have enabled for different security policies, only showing the five types: DDoS Protection, WAF, Bot Management, API Security, and Threat Intelligence.
Click Go to Policies, you will go to the policy configuration page directly.
View the updates
Flood Shield 2.0 will continuously update WAF rules, DDoS managed rules, and product features, helping you deal with the latest security threats. Click More to view the details of the updates.
- WAF managed rules: CDNetworks security experts team is continuously updating the WAF rules by tracking the latest threats and analyzing the traffic on the CDNetworks cloud, which can ensures the rules always provide high-quality protection. By default, updates are deployed every Wednesday. In case of major urgent vulnerabilities, the rules will be followed up and deployed immediately. If you have a website using manual mode, please pay attention to the updates of WAF rules and evaluate whether to upgrade them for defensing threats.
- DDoS managed rules: CDNetworks security experts team keeps tracking the latest threats and summarizes their Attack & Defense experiences. The DDoS managed rules will protect your business from application layer DDoS attacks.
- Product features: Updates such as the release of new features of the product, capability upgrades, and optimization of user experience.
View website request data and trends
Select the time range and hostnames, then click Query to view the request distribution and trends of the websites. If the observation request ratio (ratio of total requests) is too high or the attack requests suddenly increase, you can assess whether you need to adjust the security policy through log analysis.
- Total Number of Requests: The total number of requests that has accessed CDNetworks.
- Number of Mitigated: The number of attack requests detected and scrubbed by CDNetworks.
- Number of Monitored: The number of attack requests only detected and recorded in the Log by CDNetworks.
- Number of Whitelisted: The number of requests that are allowed to trigger the whitelist.