SAML Integration
Last update:2024-01-02 16:09:07
Content
1. Usage Scenario
ESA allows integration with third-party identity providers using the SAML protocol, such as Okta, OneLogin, Azure AD, Ping Identity, and Authing, etc. SAML integration allows organizations to delegate user authentication to third party IDP.
2. Operation Steps
Take ID provider Authing as example to show the whole process.
Step1: Obtain the Metadata file from the IDP management portal
1)Login to IDP management portal
2)Create a self-built app and name it “CDNetworks ESA”
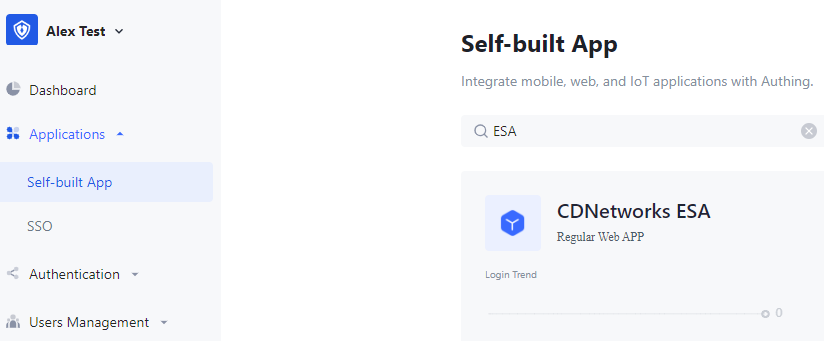
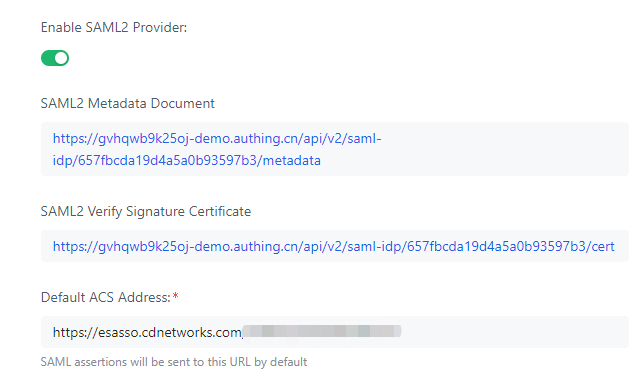
3)Enable SAML2 Provider under Protocol Configuration and download the Metadata file.
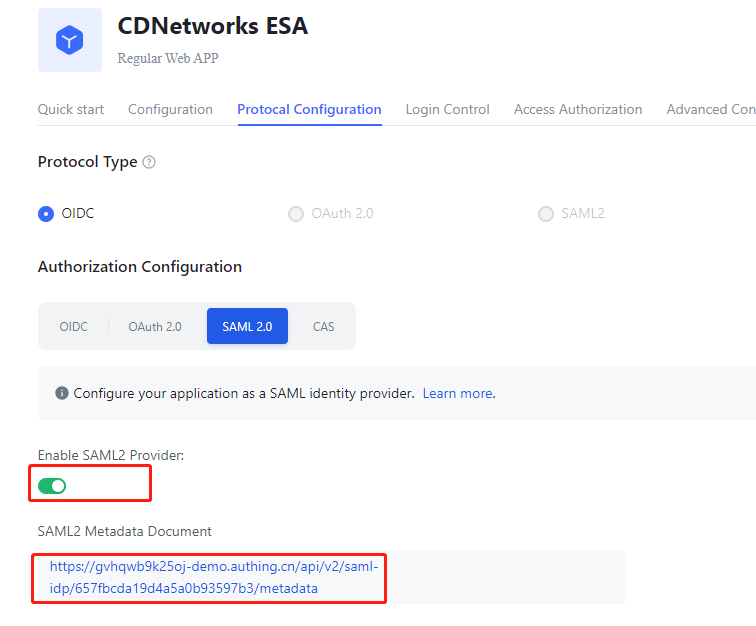
Step 2: Add IDP to ESA platform
4)Login to ESA management portal, go to ID Authentication->ID Provider-> Add IdP, select SAML.

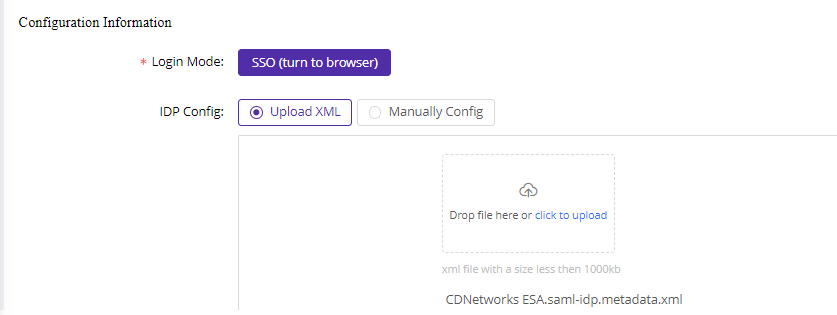
5)Fill in the basic information and upload the downloaded metadata file from the IDP management portal.
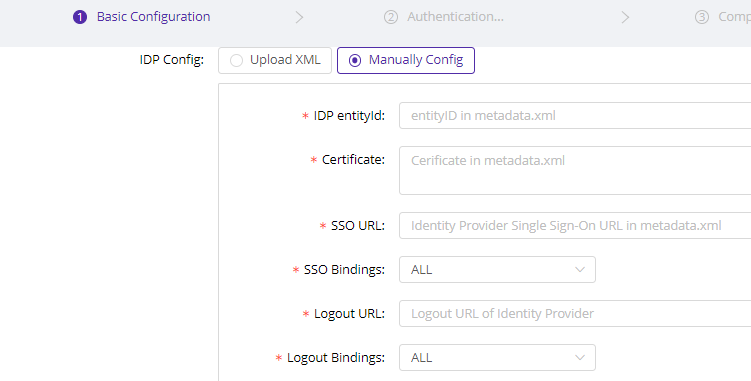
Alternatively, if unable to download the metadata, manually configure and input the necessary information obtained from the IDP.
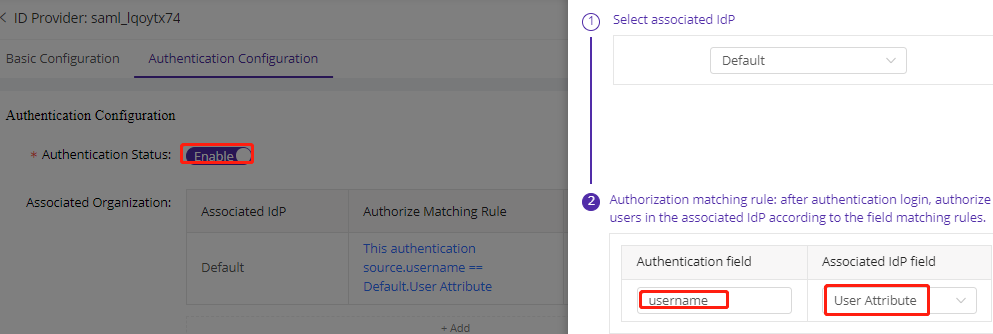
6)On the authentication configuration page, enable authentication and select the user account attribute to verify the user ID. Ensure that this attribute matches the configuration on the IDP. Refer to the IDP’s documentation for details. This step is to match your current user account/IDP with the SAML IdP, once matched, SAML IdP can verify user account correctly.
For example, CDNetworks is using AD but use OKTA as user verification provider. Then we sync AD accounts to ESA and then add OKTA under SAML as ID verification provider. When we login on ESA, we use OKTA TOTP code to verify ID.
7)Submit the configuration to complete the ESA setup and copy the SP ACS URL.
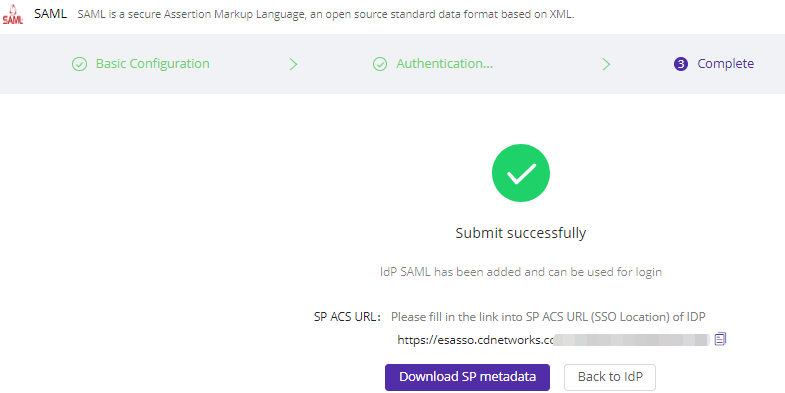
Step3: Paste SP ACS URL back to IDP
Step 4: Try login ESA with SAML account
8)Launch the ESA client and enter the enterprise ID.
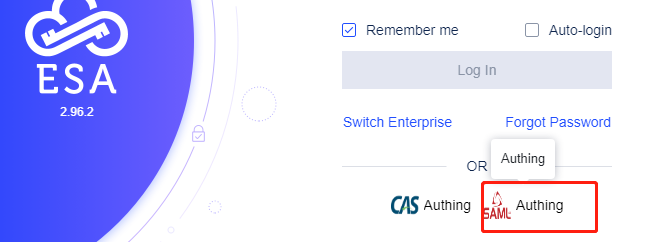
9)Select the configured IDP, which will launch a login page in the browser. Enter your SAML account credentials to log in.
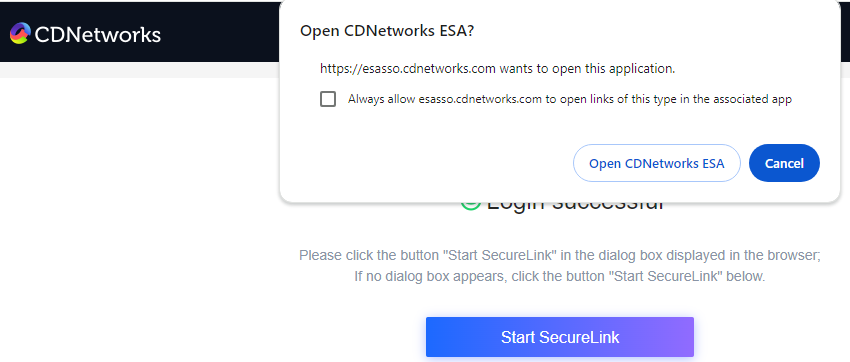
10)After filling in the credentials, a browser notice will prompt to open the ESA client. Click “Yes” to jump to the ESA client, enabling users to access authorized applications (ensure access permissions are configured).
The end of the configuration.