File Integrity Validation
Last update:2025-05-22 10:44:26
File Integrity Validation is a feature developed by CDNetworks to help customers address HTTP hijacking and content tampering issues. This feature effectively prevents such attacks, ensuring the integrity and correctness of requested files. It is particularly suited for scenarios involving large file transfers or when secure data transmission is required but full end-to-end HTTPS has not been implemented.
As internet environments become increasingly complex, hijacking and tampering have become major challenges for content providers (CPs).
- For video services, users may encounter frame drops, screen artifacts, mismatched video content, or even the inability to play videos.
- For download services, users may find that downloaded files fail to install.
What is HTTP Hijacking?
- HTTP hijacking refers to malicious man-in-the-middle (MITM) attacks that intercept and alter user requests and responses. These attacks can cause users to be redirected to incorrect or outdated files, or even to malicious websites.
What is HTTP Tampering?
- HTTP tampering involves the unauthorized modification of data packet contents. Such tampering can result in the delivery of inaccurate files or the injection of malicious code, causing users to access files where some content has been altered.
How to Implement File Integrity Validation
CDNetworks offers three solutions. Customers can choose the most appropriate one based on their business requirements and specific use cases.
| Function | Description | Suitable Scenarios |
|---|---|---|
| Response Header Token Validation | Determines if the response originates from the correct server by verifying the token in the response header | Recommended where anti-hijacking is critical, but content anti-tampering requirements are lower |
| Hash Validation (based on Origin’s Hash Value) | Verifies file integrity using the hash value provided by the origin server | Ideal for scenarios with high data security needs, where the origin can provide hash values |
| Hash Validation (based on CDN Algorithms) | Assesses file integrity by comparing hash values from CDN servers using a dedicated monitoring system | Suitable when high data security is needed, but the origin cannot provide hash value, and absolute accuracy is less critical |
Response Header Token Validation
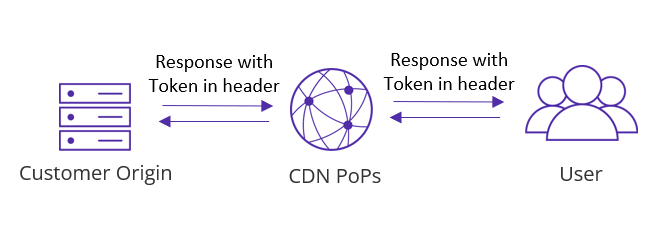
- When serving files, the server (origin or CDN) includes a token in the response header. The client (CDN or end user) then checks whether the token in the response header matches the agreed-upon rule to verify that the file comes from the correct server.
- If the validation fails, the client can initiate an HTTPS request or use a private CDNetworks protocol to retry the request, according to its configuration.
Hash Validation based on Origin’s Hash Value

- When the server (origin or CDN) serves a file, it calculates a hash value for the file content using a predefined algorithm and includes this hash in the response header sent to the client (CDN or end user).
- After the CDN caches the file, it calculates the hash using the same algorithm and compares it to the hash value from the server’s response header. If the values match, the file is confirmed as untampered. If they differ, the file is considered tempered, and the CDN client will remove the cache and may retry the request via HTTPS.
Hash Validation based on CDN Algorithms
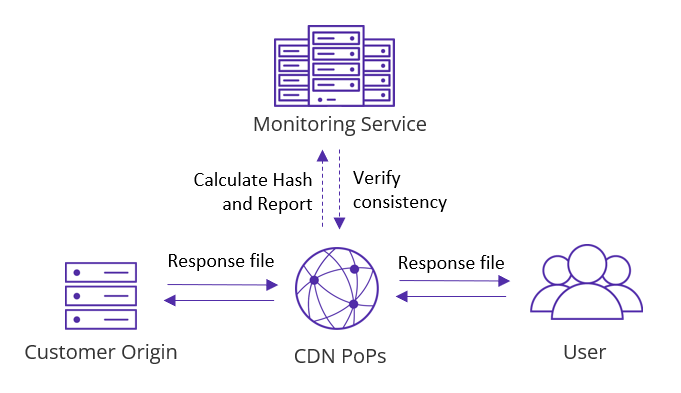
- The origin server does not provide a token or hash value when serving the file; only the file itself is returned.
- After the CDN caches the file, it calculates a hash value using CDNetworks’ internal algorithm and reports this hash to the CDNetworks monitoring system.
- The monitoring system maintains a record of hash values from all CDN servers. When a new CDN server reports its hash, the system evaluates the file’s integrity by comparing it to existing hashes.
- If inconsistencies are detected, the monitoring system triggers an alert and removes the file from that server, prompting the server to re-request the file.
- If the hashes are consistent, the monitoring system returns a successful result to the CDN server, which can then deliver the file to the user.
How to Configure File Integrity Validation
Implementing this feature involves configuring multiple options, such as HTTP headers. The setup process varies depending on the scenario, can be relatively complex, and may require support from the origin server. Please contact CDNetworks technical support in advance. Our support team will confirm your requirements and solution and will coordinate the configuration for you.
Notes
- Both Response Header Token Validation and Hash Validation based on Origin’s Hash Value require cooperation from the customer’s origin server or client.
- If origin server cooperation is not possible, consider using Hash Validation based on CDN algorithms or the CDNetworks Object Storage Service.