Restrict the Bucket Access by IPs
Last update:2024-03-28 11:09:07
Object Storage sometimes serves as the origin for the CDN. In such instances, access to the content stored within Object Storage should ideally be limited to the CDN and selected users, thereby ensuring the security of the files within Object Storage.
This tutorial will guide you on how to configure access restrictions for specific accounts, ensuring they can only access content within your storage bucket via approved IP addresses. Attempts to access content through non-approved IP addresses will be outright denied, safeguarding your content against unauthorized use.
Before You Start
Before we begin, it’s important to note the following considerations:
- We’ll use IAM (Identity and Access Management) to control the access from different accounts, which requires an available pair of AccessKey and AccessKey Secret. Thus before using IAM, please ensure that the account you intend to restrict has at least one set of these credentials.
- IAM authorizations impact only direct access to your storage bucket. The CDN back-to-origin will not be affected.
For additional details on IAM operations, please refer to the IAM documentation.
Example
Let’s assume we need to restrict sub-account “alvin” so it can access the storage only through the IP address “27.148.104.22”. Follow these steps to achieve this:
- Sign in to the CDNetworks console and navigate to IAM > Permissions > Policies, and click Add Policy to create a new permission policy.
- Select Visualized, choose Object Storage (wos) under Non-CDN Product Services, then click Next.

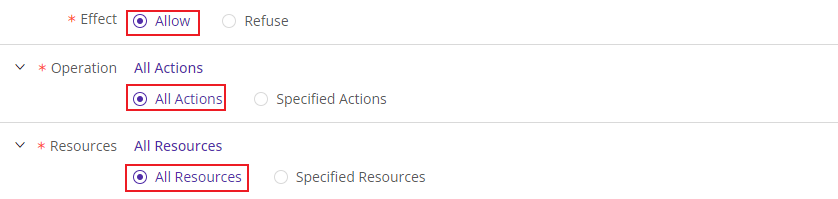
- Select Allow, All Actions and All Resources.
- Add a restriction condition by selecting SourceIp as the keyword, StringNotEquals as the condition, and enter the permitted IP address “27.148.104.22” in the space provided. Complete the form and proceed by clicking Next.

- Name your policy accordingly and advance to the next step by clicking Next.
- Allocate this permission to the targeted account by selecting it and finalizing the process with Finish.

To verify the effectiveness of your IAM configuration, consider the following tests:
Verify on console
Log into the sub-account “alvin”. If access attempts to Object Storage via the console using an unauthorized IP address (other than “27.148.104.22” for example), result in no buckets being displayed and a notification stating “There is no corresponding access rights”, your IAM permissions are correctly set.

Verify by accessing a file URL
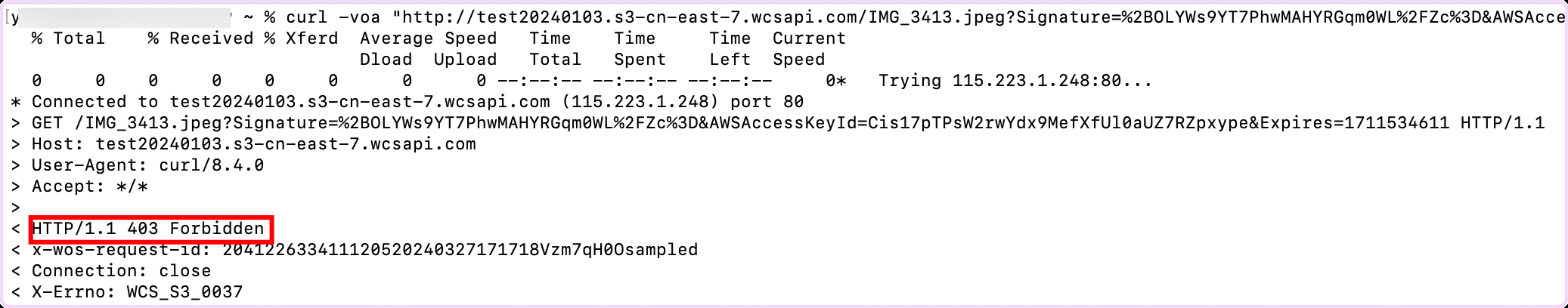
Copy an accessible URL from any file within your storage bucket and attempt to access this file via the URL, for example, using the command line:
curl -voa "http://test20240103.s3-cn-east-7.wcsapi.com/IMG_3413.jpeg?Signature=%AHYRGqm0WL%2FZc%3D&AWSAccessKeyId=Cis17pTPsW2rwYdxaUZ7RZpxype&Expires=14611"
A 403 Forbidden response confirms the IAM configuration is active and functioning as intended.