Login & Password Security
최신 업데이트:2024-01-03 09:28:29
Content
1. Usage Scenario
To enhance account security, ESA offers a range of login and password security features. If a user’s behavior triggers the security policies, a notification alert will be sent to the designated email address. It’s important to note that these security policies apply exclusively to local accounts. Accounts synchronized from a third party ID provider should be managed on the IDP, not on ESA.
2. Operation Steps
2.1. Common Settings
1)Policy Action: When a user triggers a security policy, their account will be disabled or locked.
- Account disabled: administrator must manually enable the account on Console.
- Account lockout: It will automatically unlock after reaching the lock duration.
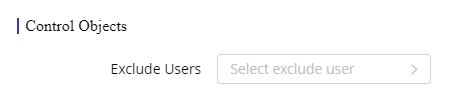
2)Exclude Users: When configuring the policy, it is by default applied to all local users. If you want to grant special permission to someone, add the user to the exclude user list. Once added, the user will not be checked by this policy.
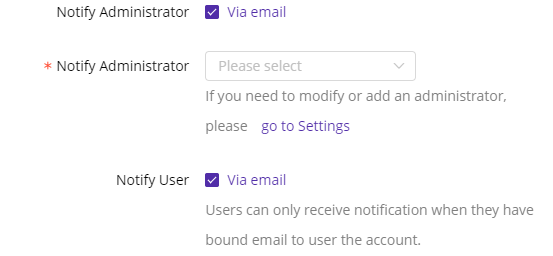
3)Notification: When a user triggers the policy, you can configure to notify only the administrator or also notify the user.
- Notify Administrator: You need to add the administrator to the contact list first so that the admin email can be shown on the list.
- Notify User: You need to bind the user’s email address under Users->User Details–> User Information first.
2.2 Account Security Policies
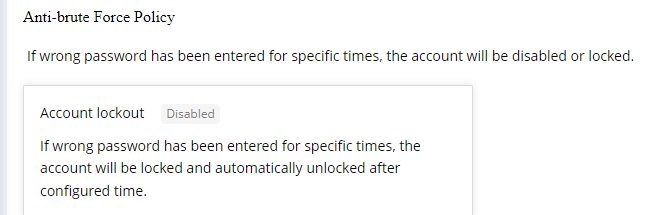
1)Anti-brute Force Policy
Use case: When a user enters the wrong password a specified number of times within a specific time period, the account will be blocked or disabled.
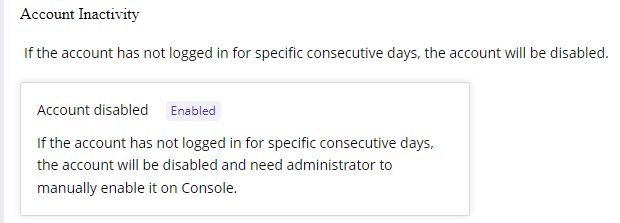
2)Account Inactivity
Use case: If a user account remains inactive for a set number of consecutive days, it will be disabled, and an administrator will need to manually enable it in the Console.
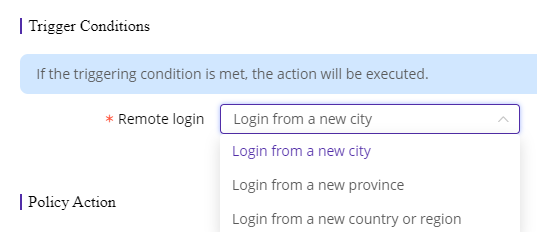
3)Remote Login Alert
Use case: When a user account is found to be logged in from a remote location different from the last login, a notification alert will be sent to the administrator or user.
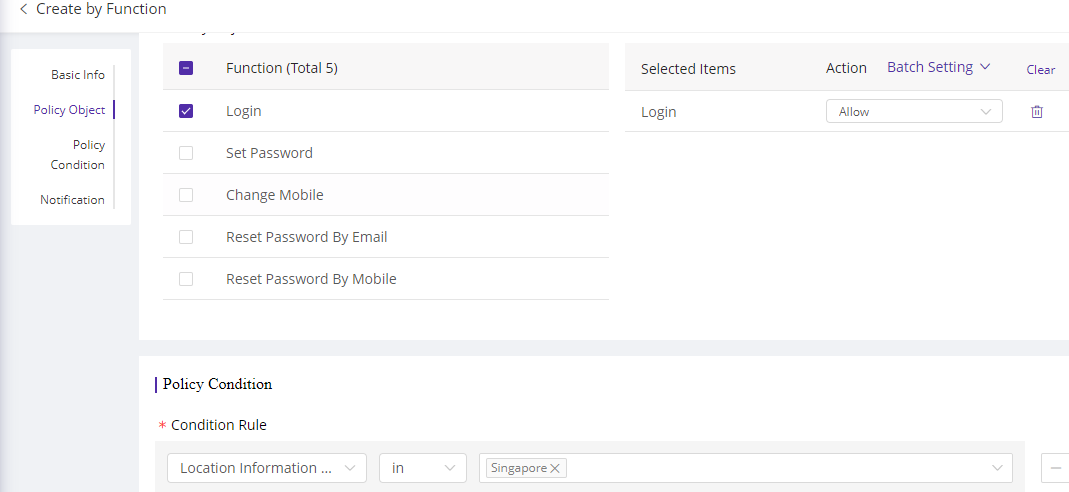
If you want to block logins from remote locations, you can create a Function Access Control policy in Dynamic Authorization to allow user logins only from specified locations, such as only allowing logins from Singapore.
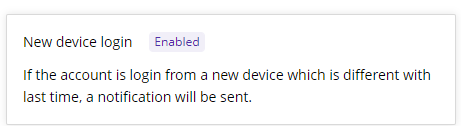
4)New Device Login Alert
Use case: When a user account is found to be logged in from a new device different from the last login, a notification alert will be sent to the administrator or user. If you want to block user logins from unknown devices, you can create a Function Access Control policy in Dynamic Authorization to allow user logins only from authorized devices.
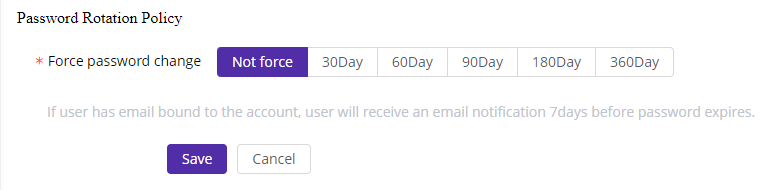
5)Password Rotation Policy
Use case: This policy forces users to change their password after a specific number of days. If a user has an email account linked to their account, they will receive an email notification seven days before the password expires. Upon receiving the email, the user should manually change the password on the ESA client before expiration. Otherwise, the account will be disabled, and an administrator will need to reactivate it.
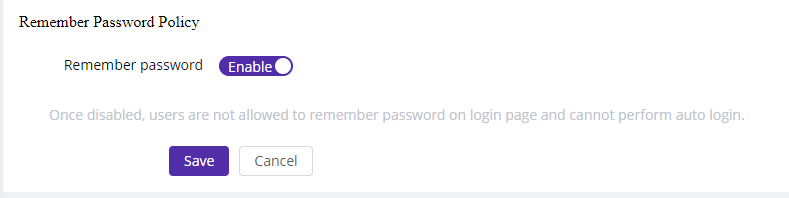
6)Remember Password Policy
Use case: This policy configures whether users are allowed to choose the “remember password” option when login. If not allowed, the user will need to enter their password each time and cannot use the auto-login feature.
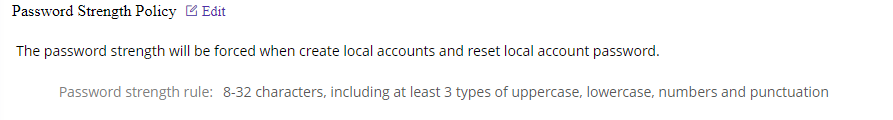
7)Password Strength Policy
Use case: This policy configures the password strength requirements for users when they attempt to change their password.