Authentication
最終更新日:2025-09-22 10:03:22
トランスコーディングリクエストを行う際、Authorizationヘッダーに認証トークンを必須で含める必要があります。このトークンは許可されたリクエストのみが処理されることを保証するセキュリティ対策です。
重要: トークンには
AccessKeyが含まれ、AccessKey Secretを使用して暗号署名されます。操作前に必ず専用のAccessKeyとAccessKey Secretを取得してください。
トークン形式
認証トークンは以下の形式に従います:
Token = [AccessKey]:[EncodeSign]
各要素の説明:
AccessKey:固有の公開識別子EncodeSign:URLセーフBase64エンコードされたHMAC-SHA1署名
認証トークン生成プロセスは以下の2段階で構成されます:
EncodeSignの生成Tokenの構築
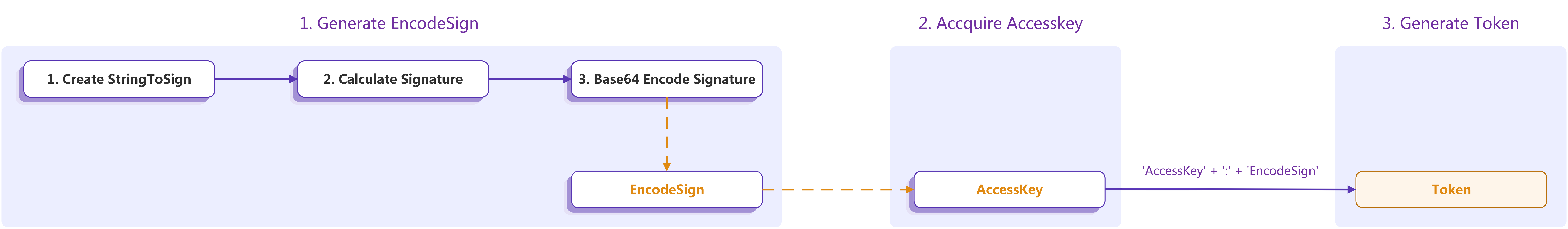
ステップ1:EncodeSignの生成
EncodeSignはStringToSignとAccessKey Secretを変換して生成されます:
EncodeSign = Urlsafe_base64_encode(HMAC_SHA1(StringToSign,AccessKey Secret))
StringToSignの構築
メディア処理リクエストの場合、StringToSignは以下の形式で構成します:
StringToSign = '/fops' + '\n' + [Request Body]
/fops:固定操作識別子\n:改行文字[Request Body]:トランスコーディングリクエストの生データ
例(リクエストボディがbucket=[bucket_name]key=[file_to_process]fops=[processing_operations]の場合):
/fops\nbucket=[bucket_name]key=[file_to_process]fops=[processing_operations]
注:実際のリクエストではBase64エンコードされた文字列を使用しますが、説明のためここでは生データを表示しています
署名の計算
AccessKey Secretを鍵としてHMAC-SHA1署名を生成:
Signature = HMAC_SHA1(StringToSign, AccessKey Secret)
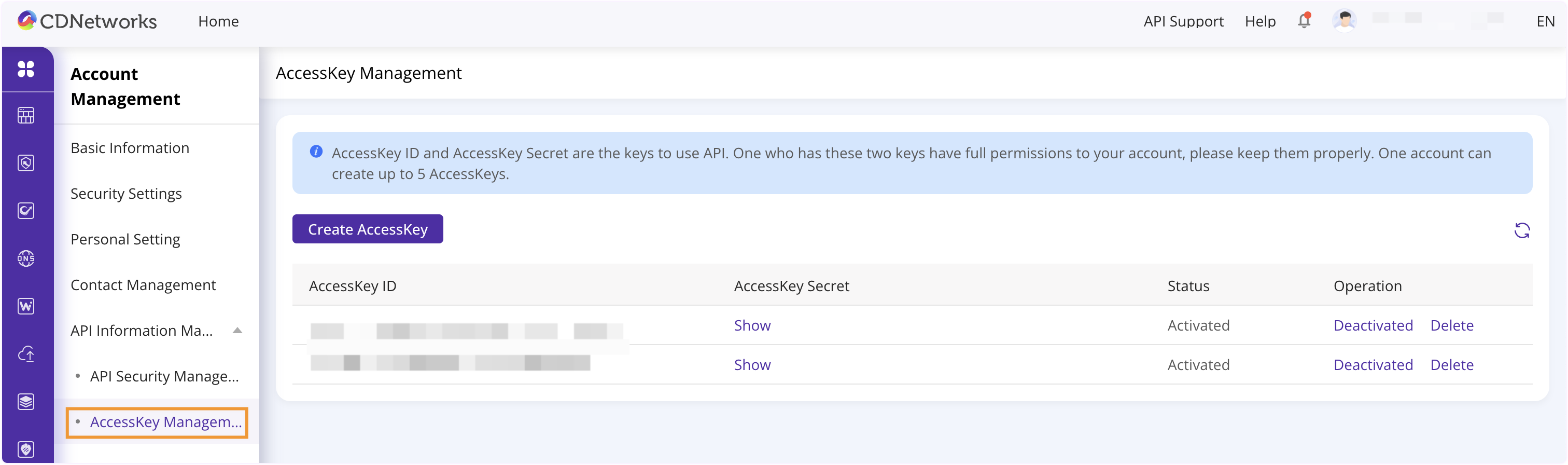
AccessKeyとAccessKey Secretは以下から取得可能:
Basic Information > Account Management > API Information Management > AccessKey Management
HMAC-SHA1実装リファレンス:
Base64エンコード
署名結果をURLセーフBase64エンコード:
EncodeSign = Urlsafe_base64_encode(Signature)
ステップ2:トークンの構築
AccessKeyとEncodeSignを組み合わせて最終トークンを生成:
Token = [AccessKey]:[encodeSign]
生成したトークンはトランスコーディングリクエストのAuthorizationヘッダーに含めてください。
実装例
実際のトークン生成コードサンプルは以下を参照:
Authentication Token Generation Examples
これらのサンプルコードは実装の詳細を理解し、アプリケーションへの迅速な統合を可能にします。