鉴权方法
更新时间:2025-09-22 10:03:22
当你向系统发起转码请求时,必须在 Authorization 请求头中包含一个鉴权凭证(Token)。这个Token是为了确保只有授权的请求才会被处理。
重要提示:Token包含您的
AccessKey,并使用AccessKey Secret进行加密签名。操作前请确保已获取专属的AccessKey和AccessKey Secret。
鉴权凭证(Token)格式
鉴权Token遵循以下格式:
Token = [AccessKey]:[EncodeSign]
其中:
AccessKey:您的唯一公共标识符。EncodeSign:基于 HMAC-SHA1 算法签名后,并进行 URL 安全的 Base64 编码所得的字符串。
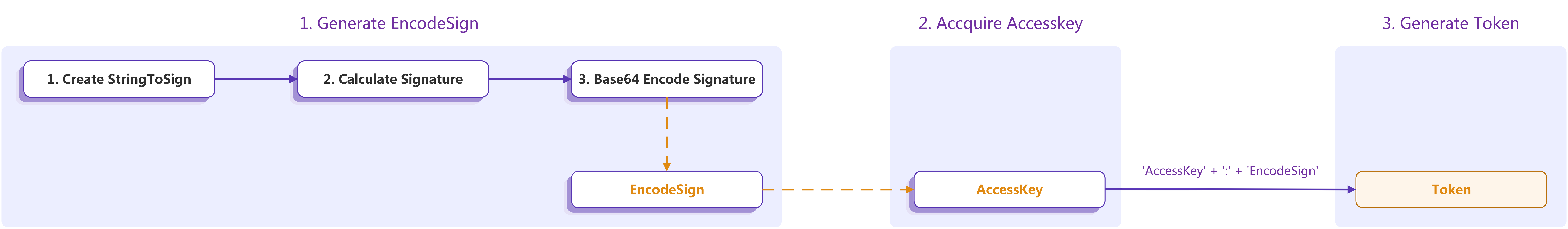
鉴权Token生成流程包含以下两个核心步骤:
- 生成
EncodeSign - 构建
Token
接下来是详细步骤
步骤1:生成EncodeSign
EncodeSign通过对StringToSign和AccessKey Secret进行多重转换生成:
EncodeSign = Urlsafe_base64_encode(HMAC_SHA1(StringToSign,AccessKey Secret))
具体流程如下:
构建StringToSign
StringToSign根据请求类型构建。对于媒体处理请求,其遵循格式:
StringToSign = '/fops' + '\n' + [Request Body]
/fops:固定操作标识符\n:换行符[Request Body]:转码请求内容
示例:若原始请求体为bucket=[bucket_name]key=[file_to_process]fops=[processing_operations],则:
StringToSign = /fops\nbucket=[bucket_name]key=[file_to_process]fops=[processing_operations]
注意:此处的请求体示例为便于理解使用原始字符串展示,实际请求可能使用Base64编码后的字符串
计算签名
一旦您构造完成了StringToSign,接下来使用AccessKey Secret作为密钥,对StringToSign进行HMAC-SHA1签名计算:
Signature = HMAC_SHA1(StringToSign, AccessKey Secret)
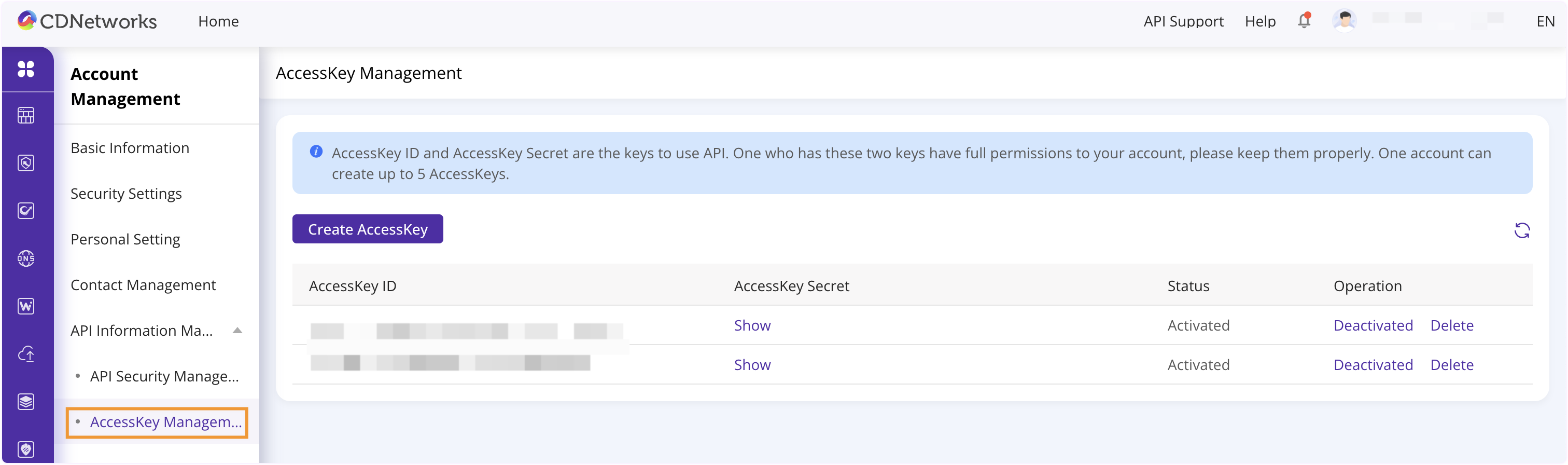
单击您的账户头像后,您可以通过导航到 基本资料 > 账户管理 > 用户信息管理 > AccessKey管理, 来获取AccessKey和AccessKey Secret。
HMAC-SHA1算法实现参考:
Base64编码签名
最后,对签名结果Signature进行URL安全Base64编码,获得最终EncodeSign:
EncodeSign = Urlsafe_base64_encode(Signature)
步骤2:构建Token
将生成的EncodeSign和获取的AccessKey按以下格式组合,形成最终鉴权Token:
Token = [AccessKey]:[encodeSign]
此Token需包含在转码请求的Authorization请求头中。
示例
关于Token生成的具体代码实现和可执行示例,请参考:
这些示例可帮助您快速理解实现细节,并将凭证生成功能集成到应用中。