缓解资源耗尽教程
更新时间:2025-01-16 14:15:51
场景 1:限制对关键 API 接口的高频访问
示例:票务网站 www.ticket.com 今天通过接口 /api/BuyTicket 在周一 10:00 - 11:00 (GMT+8) 销售演唱会门票。为了防止不当囤票,有必要限制访问该接口的频率为每10秒不超过100次。如果超过此阈值,则应阻止该客户端 IP 对该接口的访问10分钟。配置步骤如下:
1. 创建频率限制规则
- 转到 防护配置 > 共享配置 > 频率限制。
- 点击 新增规则。
2. 配置规则信息
-
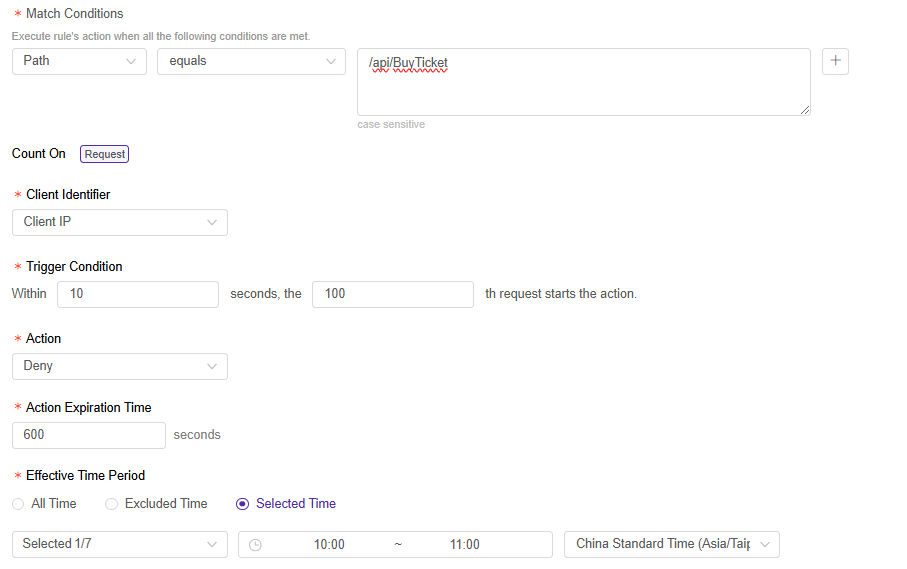
配置 匹配条件:选择对象为 “路径”,操作符为 “等于”,并输入内容 “/api/BuyTicket”。
-
配置 计数:选择客户端标识符为 “客户端 IP”,触发条件为 “在10秒内,第100次请求开始执行动作。”,动作为 “拒绝”,并设置处理动作持续时间为 “600秒”,最后设置生效时间段为 “周一,10:00 - 11:00,GMT+8”。
-
点击 确认 创建此规则。
配置如下所示:
3. 关联主机名
- 返回 频率限制 页面,找到创建的规则。
- 点击
 ,关联主机名,从主机名列表中选择 “www.ticket.com”,然后点击 确认 以发布此规则。
,关联主机名,从主机名列表中选择 “www.ticket.com”,然后点击 确认 以发布此规则。
场景 2:缓解爬虫工具对网站的访问压力
1. 创建策略
- 转到 防护配置 > 安全策略管理。
- 找到您要保护的主机名,点击
 。
。 - 进入 Bot管理 标签。
2. 配置策略信息
-
配置 基本检测:
- 为网站特定的监控工具(如果存在)允许通行。根据监控工具的特性,在自定义Bot中创建规则,并将动作设置为跳过。了解更多。
- 允许搜索引擎爬虫,以确保网站的SEO效果。在已知Bot中,将搜索引擎类别的动作设置为允许;如果没有这种需要,您也可以设置动作为拒绝。
- 阻止常见的商业或开源工具。在基于用户代理的检测中,将低版本用户代理、假用户代理、自动化工具和爬虫工具等类别的动作设置为拒绝。
-
配置 基于客户端的检测:
在发布到生产环境之前,建议通过页面底部的 “发布变更 - 发布到预发布” 按钮进行测试,以验证网页机器人检测的JS SDK与您网站的兼容性。
3. 启用策略
确认配置正确后,点击页面底部的 发布变更 按钮,并点击 发布到生产环境 按钮以使配置生效。
场景 3:阻止不符合正常业务访问逻辑的行为
对于不符合正常业务访问逻辑的行为,例如自动化工具绕过页面访问直接对某个接口发起持续攻击,建议在场景2的基础上配置工作流检测策略以加强保护。有关配置示例,请参阅工作流检测详情。
本篇文档内容对您是否有帮助?
有帮助
我要反馈